Explain at Least Two 2 Different Risk Assessment Methodologies
Types of assessment methods Using a range of assessment methods helps produce valid decisions and recognises that learners demonstrate competence in a variety of ways. Risk Probability and Impact Assessment.

Types Of Financial Statements Finance Investing Accounting And Finance Financial
There are two types of assessment formative and summative assessments.

. Using the ThinkSafe steps 1. A hazard is anything that could hurt you or someone else. Assess the Risk Risk Assessment Make the Changes Risk Control At work you can use these three ThinkSafe steps to help prevent accidents.
This type of assessment is generally. ISO 27001 requires that risk assessment have five main steps the same ones that are explained in the section about the risk assessment methodology. Explain How to Monitor Children and Young Peoples Development Using Different Methods.
Based on the landmark work of the Committee of Sponsoring Organizations of the Treadway Commission COSO 2 in the 1990s its seminal Enterprise Risk Management. Systematic risk impacts everything. Risk identification listing assets threats and vulnerabilities Assigning risk owners persons responsible for risk Risk analysis assessing consequences and likelihood.
Another approach is to send out a questionnaire and schedule an in person. This method involves looking into the likelihood of each risk and the ways it may affect separate project objectives such as those tied to budget schedule and performance. Examples of workplace hazards include.
A decent beginning is to walk simply close to your work environment and think about with respect to any dangers. Method Description Direct observation Assessed in real time in the workplace. The hugest qualities of your hazard appraisal are precisely distinguishing the potential dangers in your work environment.
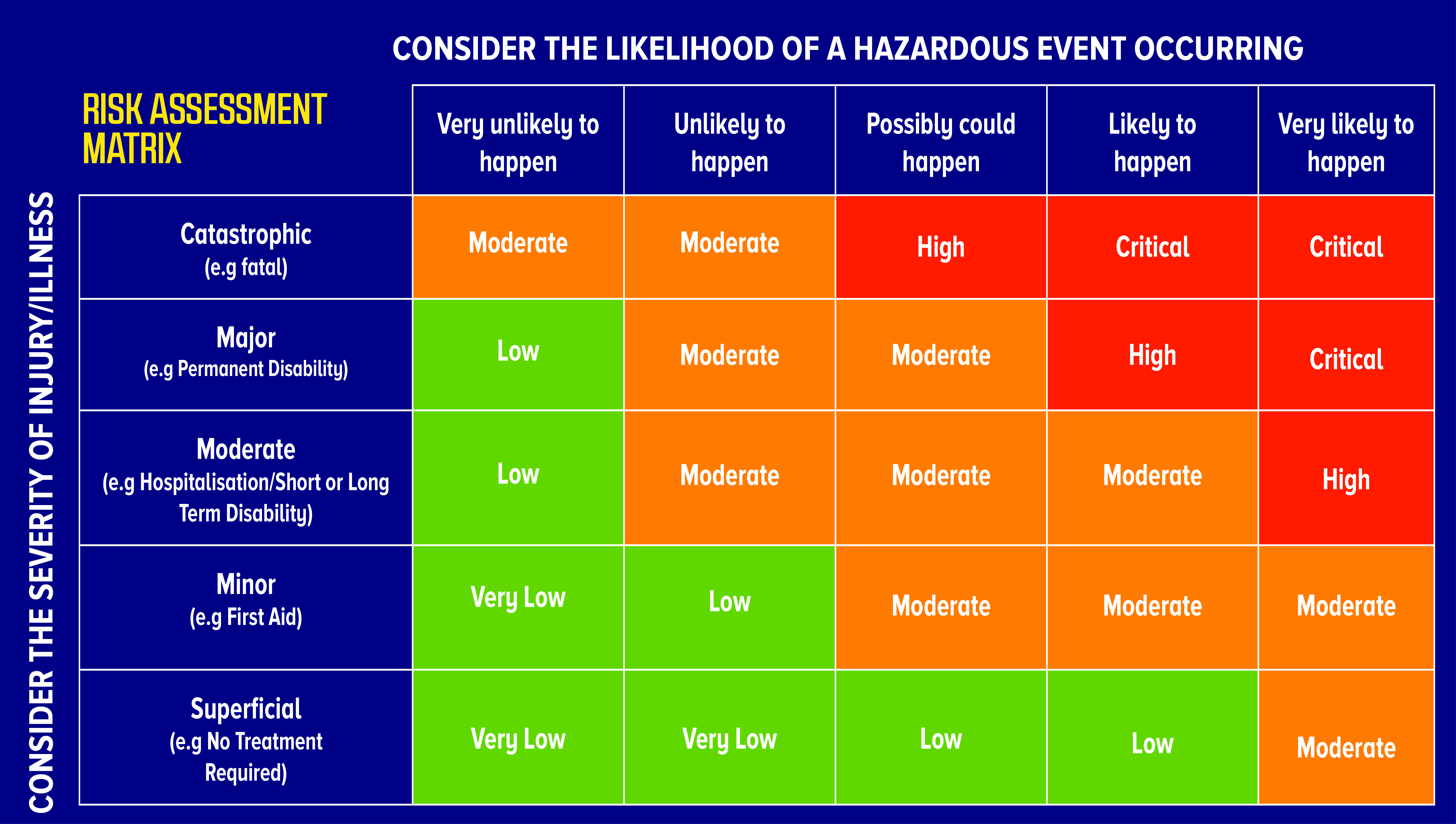
R elevant the activity is suitable and realistic relates to what is being assessed and will give consistent results. Describe the key approaches to identifying threats relevant to a particular organization. Explain at least two 2 different risk assessment methodologies.
That way you get a detailed risk assessment and understanding of the resource up front but can scale back the resource effort over time. A chievable the activity can be achieved at the right level. Enterprise risk management ERM 1 is a fundamental approach for the management of an organization.
Early intervention is crucial to lessen the likelihood of developmental delay. A range of assessment methods are outlined in the table below. M easurable the activity can be measured against the assessment requirements allowing any gaps to be identified.
It is necessary to monitor child development to ensure that assessments can be made to help identify children at risk and prevent those who are not yet at risk becoming at risk. Describe the key approaches to identifying threats relevant to a particular organization. There are many different methods of monitoringobserving and recording children and young people behaviour and performance.
CYPCore31-31 Explain how to monitor children and young peoples development using different methods. Risk Factor Analysis RFA Risk Factor Analysis RFA is one of the many methods of risk analysis that follows a qualitative approach. This is especially so where the environment or human life is at risk.
Access control is a core concept in cybersecurity so naturally its covered on the CISSP certification examCISSP domain 5 covers identity and access management and objective 54 within that domain is Implement and manage authorization mechanismsThere are six main types of access control models all CISSP. Interview for the first assessment and a questionnaire for each subsequent assess-ment for that same resource. Include in other assessment methods Demonstrates concern about gathering feedbackinformation Potential Disadvantages Information on student learning perception and opinion considered to be indirect data Good surveys and questionnaires are difficult to develop Voluntary participation may result in biased results.
You can learn a lot by observing employees. Explain at least two 2 different risk assessment methodologies. Learning objective Place in Assessment 21 Explain the purpose of correctly receiving checking and Question 1 Page 3 sorting incoming and outgoing mail or packages 22 Identify different internal and external mail services Question 2 Page 3 available to organisations 23 Describe the methods of calculating postage charges for Question 3 Page 4.
Explain the relationship between access and risk and identify the tradeoffs of restricting access to the organizations assets. The two safety jobs combine to mitigate and prevent the chances that incidents occur - and ensure that assets equipment and people are kept as safe as possible. Experienced managers and organizations can adapt SHAMPU to existing practices to customize risk assessment according to situational requirements.
Describe two models and methods for operational planning. Qualitative methods are a good starting point when you begin your assessment. The two major types of risk are systematic risk and unsystematic risk.
Frayed electrical cords could result in electrical shock. In this case negative effects are threats and positive effects are opportunities. These methods can be useful for describing a situation and can provide insight for your intervention approach.
This type of system is a comprehensive way to identify factors that can affect the. Explain at least two 2 different risk assessment methodologies. Describe different types of assets that need protection.
Remember however that behaviors may be changed by the very act of observing. It is the general broad risk assumed when investing. Explain at least one budgeting process used by your oganisation.
Explain the role of. Performing a Security Risk Assessment. Hazard identification and risk assessments are the first line of defence and hopefully the only line needed to.
Explain the relationship between access and risk and identify the tradeoffs of restricting access to the organizations assets. A number of stakeholders will have requirements in place that must be taken into account in any risk management process. Hazard identification and risk assessments form the basis of proactive project safety and prevention.
Describe different types of assets that need protection. Access control and the CISSP certification.

Hammer Candlestick Chart Pattern Candlestick Chart Trading Quotes Trading Charts
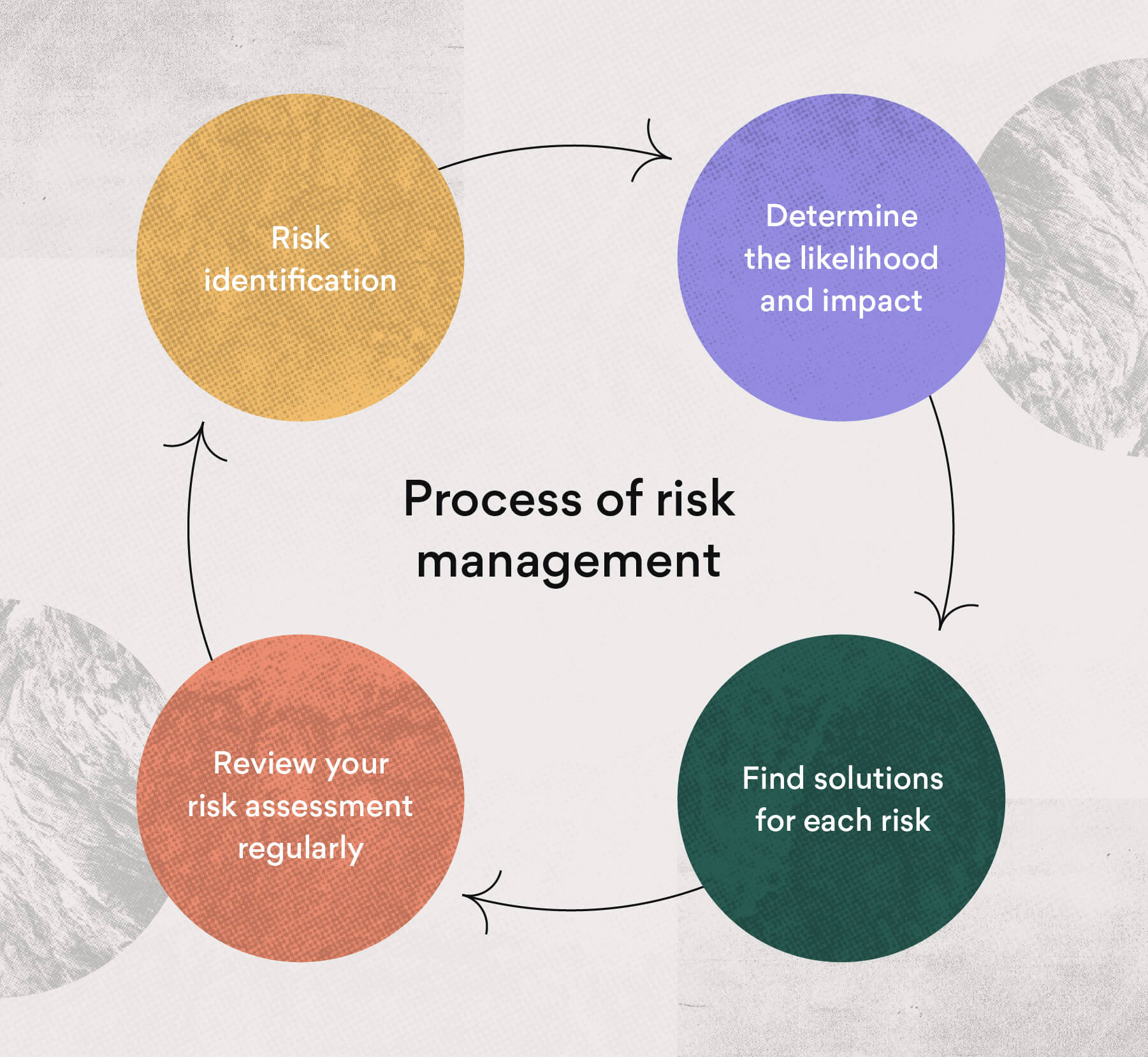
7 Common Project Risks And How To Prevent Them Asana

Technology Readiness Level Technology Technology Trends Levels

Interesting Representation Concept Infographic Infographic Design Data Visualization

Risk Impact Assessment And Prioritization The Mitre Corporation

How To Define Scope For Your Project Project Charter Projects Scope
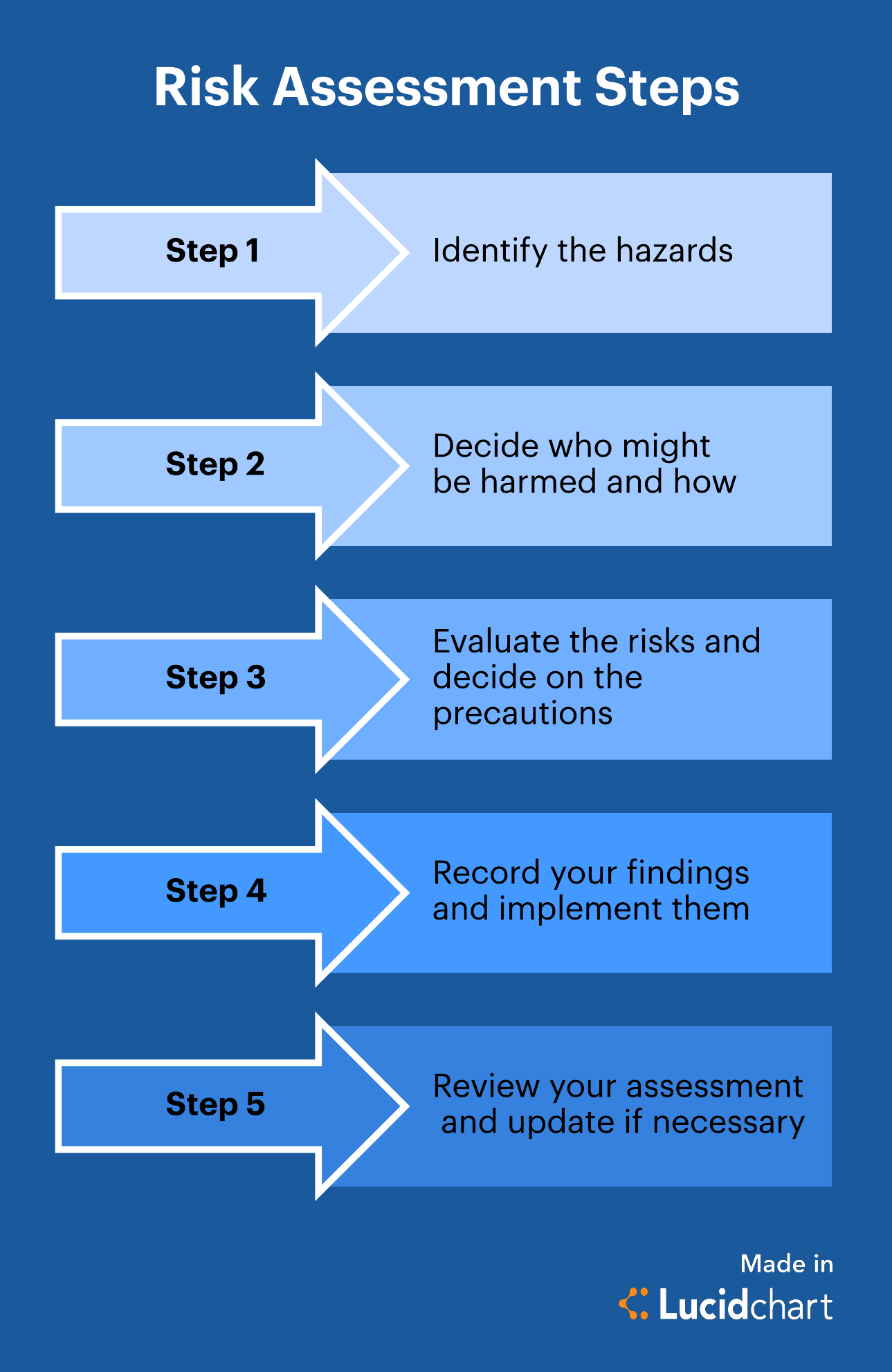
A Complete Guide To The Risk Assessment Process Lucidchart Blog

Mgt325 Mgt 325 Week 4 Dq 2 Mitigated Risks Http Www Scribd Com Doc 133871512 Mgt325 Mgt 32 Relationship Management Customer Relationship Management Crm

Hazard Identification And Risk Assessment

5 Steps To Any Effective Risk Management Process Lucidchart

Angel Investors Angel Investors Finance Investing Finance Saving

Safety Assessment Assessment Firefighter Humor Safety Audit

Technical Analysis For Dummies Ebook By Barbara Rockefeller Rakuten Kobo Technical Analysis Fundamental Analysis Dummies Book
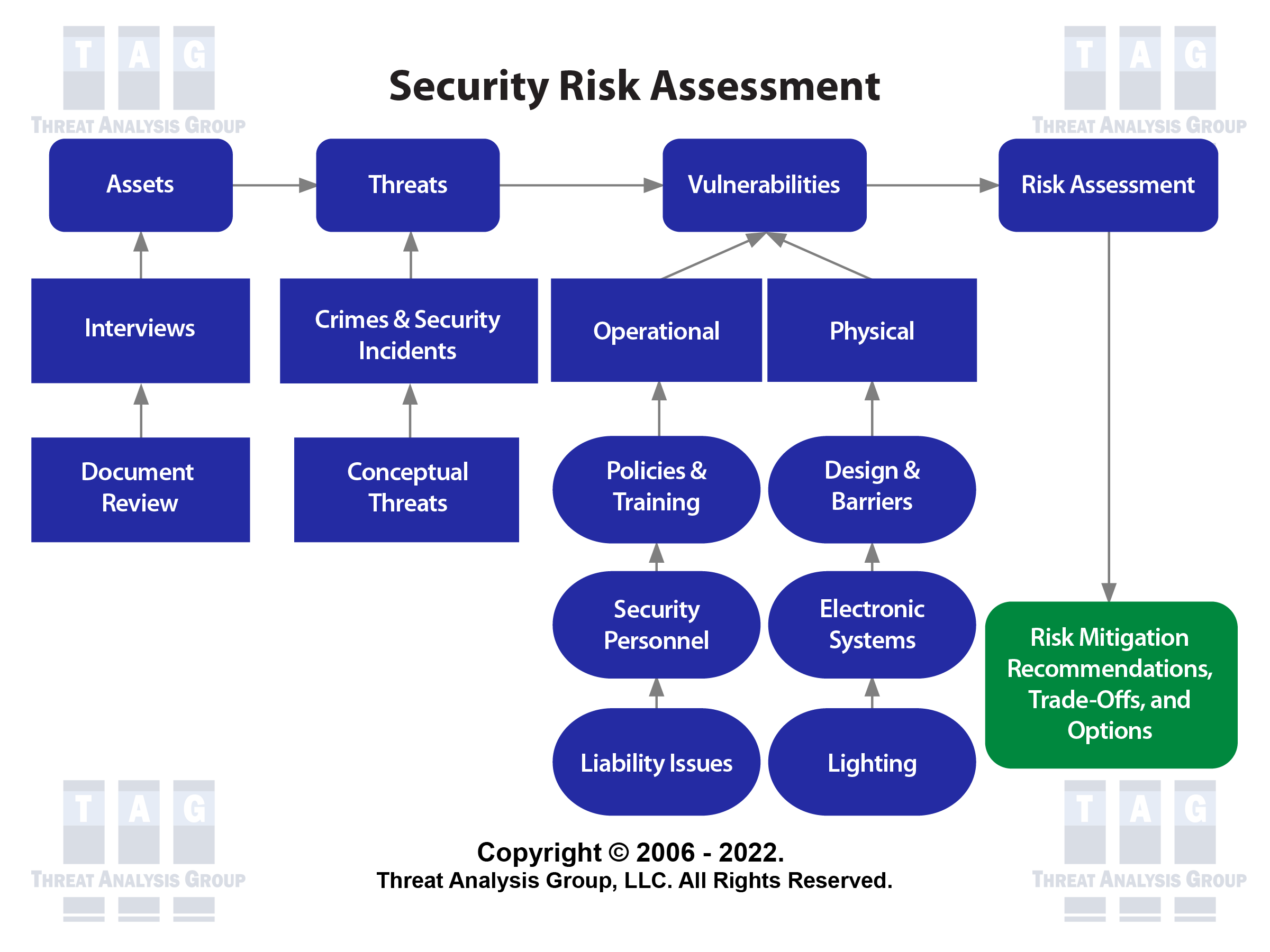
Security Risk Management Threat Analysis Group

Healthy Lifestyle Assessment Task Healthy Eating And Exercise Social Emotional Activities Student Created Primary School Education

A Complete Guide To The Risk Assessment Process Lucidchart Blog

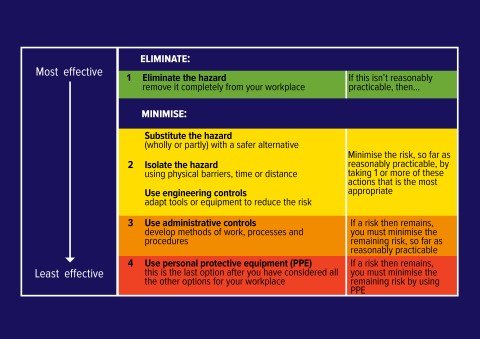
Comments
Post a Comment